How to install SABER for Your IPT?
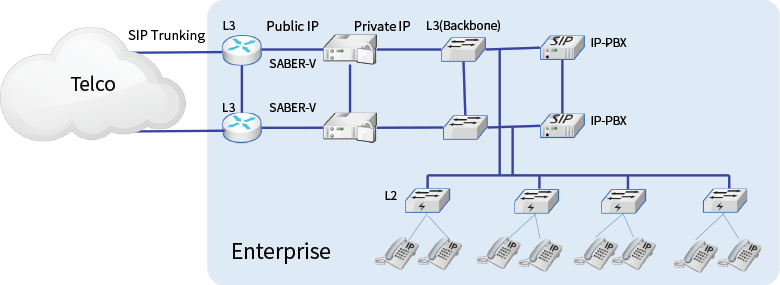
This diagram shows how the SentryAll should be implemented in order to secure IPT from VoIP Cyber threats.
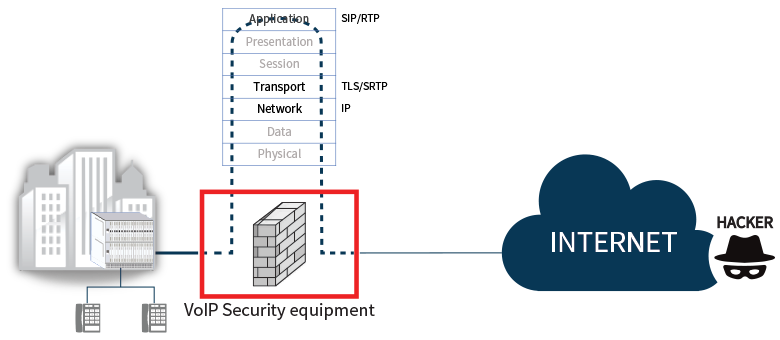
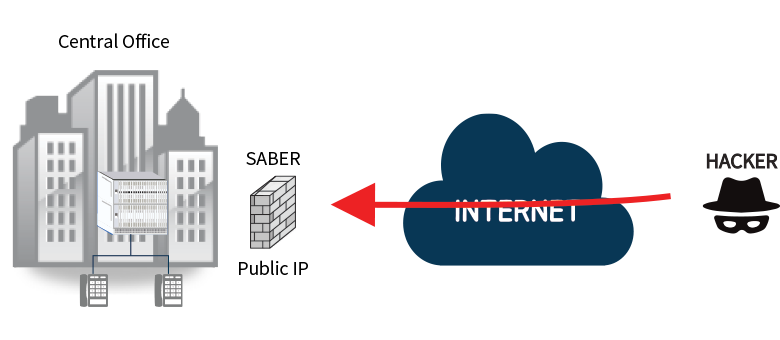
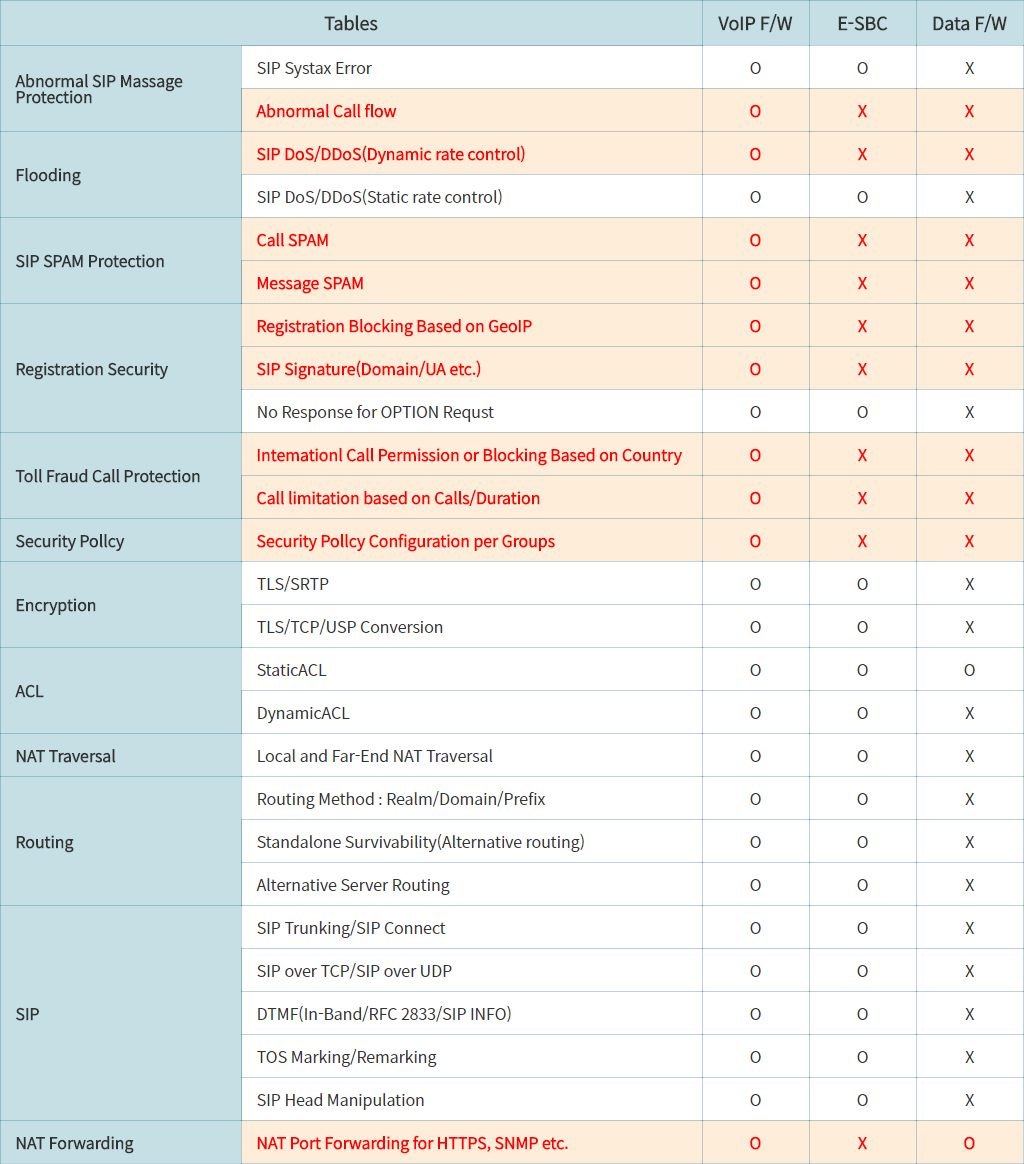
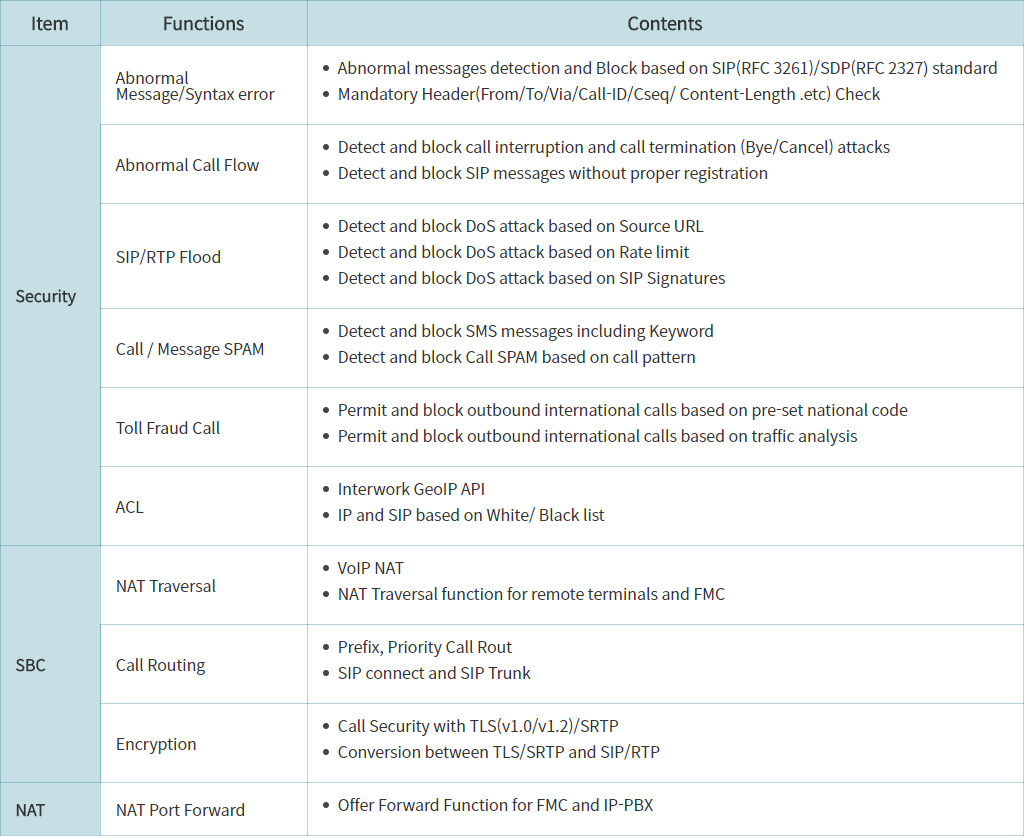
This is the most common scenario for All SIP network, SentryAll is doing main 2 features, Session Border Controller and VoIP Security In the past, IP administrators used to install NAT/Firewall for secure the IPT, and they believe the firewall would protect the VoIP Attacks But it would fail to detect VoIP Attacks, because most of firewall has no feature to handle SIP messages to attain RTP port info. for communication. So it should open all UDP port, and it causes to be victims of VoIP Cyber criminal.
Data Firewall may be optional but when you want to install it in front of SentryAll, you should set IPS mode and turn off SIP ALG feature.
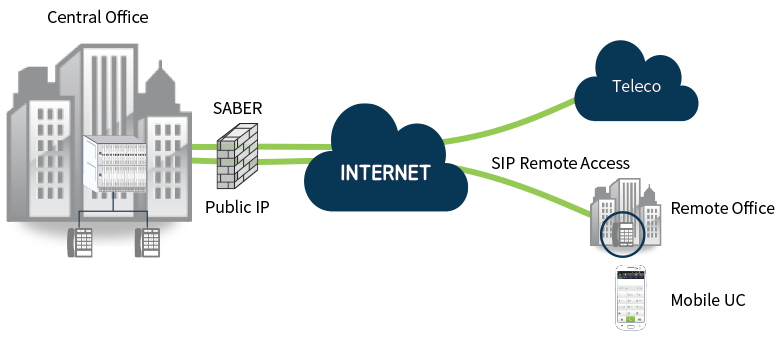
Back to this diagram, SentryAll should have public IP address and role as Session Border Controller that enables to solve NAT Traversal issue and manipulates SIP messages for interworking with Telco, sometimes IP-PBX doesn’t meet SIP requirement of Telco.
SentryAll has many references for interworking with Global IP-PBX vendors, Cisco, Avaya, Nortel, SAMSUNG, ERICSSON, Asterisk.
It would scan all SIP messages with its own security algorithm at the same time.
As for the redundancy, it provides switchover for the seamless service when active system doesn’t work normally based on periodic health check.







 +82 (0)2-6932-1630
+82 (0)2-6932-1630 sales@egistech.co.kr
sales@egistech.co.kr